Security for the price of a single latte
Every operating system and device has its security tools. If you use a desktop computer, you will be familiar with the wide range of firewalls, virus and malware checkers, and general security advice out there.
But what about your smartphones and tablets? With more people switching to mobile computing, and more tablets being used as de-facto computers, the need for a mobile security solution becomes ever more pressing.
A new solution for iOS devices has presented itself, called iVerify. At $5, it will put off the freebie-searching crowd, but it’s worth sacrificing your daily latte in exchange for peace of mind.
But….iOS Devices Can’t Be Hacked!
There’s a bit of a dangerous delusion that iOS devices are impregnable. That the encryption on them makes them immortal to any hacking attempts. That is wrong.
It is true that iOS devices have extremely good encryption features (provided you remember to switch them on!). But nothing is guaranteed. Bugs are being found all the time, including ten bugs in iMessage alone.
iVerify monitors for any potential security vulnerabilities and flags up anything it deems suspicious. It also gives you a checklist of things you need to do to lock down your phone completely to make it even more difficult for anyone to access your phone.
Setting Up iVerify for iOS
iVerify works on both the iPhone and iPad. Buying for one will give you the version for the other, so we strongly suggest setting the app up on both devices if you have both.
- When the app has been downloaded, open it up and click the green Continue button.
- This then opens up the main screen to show what it believes to be the four main important areas of security – Device Scan, Touch ID, Screen Lock, and your current iOS Version.
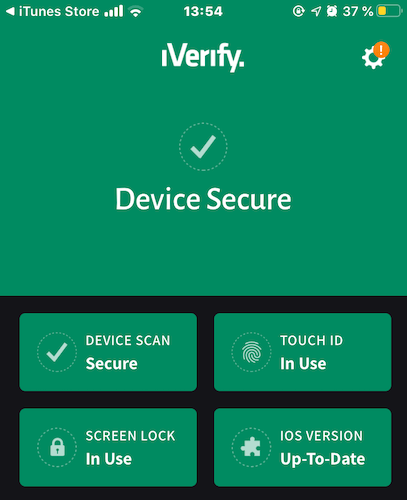
- Since I am using and updating them all, they are all currently green. But if any of them were disabled or out-of-date, they would show up as red, requiring immediate attention.
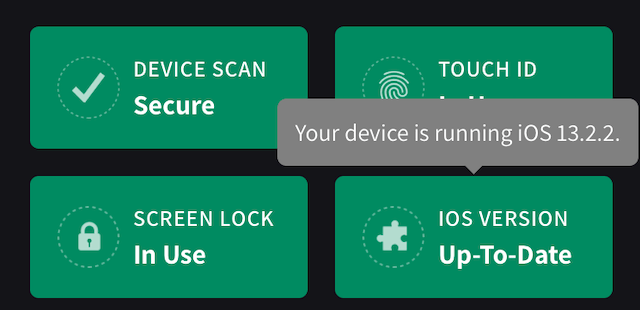
- If you lightly tap on one of the buttons, it will give you relevant information.
- If you now scroll further down the page, you will see checklists of security precautions you can now take to lock down your device even more.
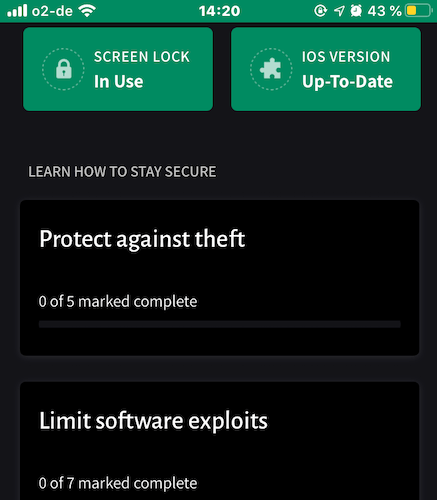
- If you tap on the first one, Protect against theft, you will get a list of iVerify’s recommendations in that category.
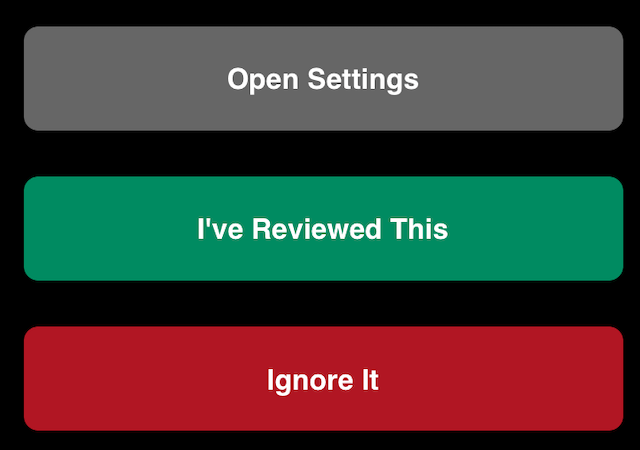
- What is a bit of a minus is that iVerify does not check to see if you have already done these things. It just assumes that you haven’t. If you find something you have already done, tap on it, scroll to the bottom, and then tap I’ve Reviewed This. It will then be marked as complete.
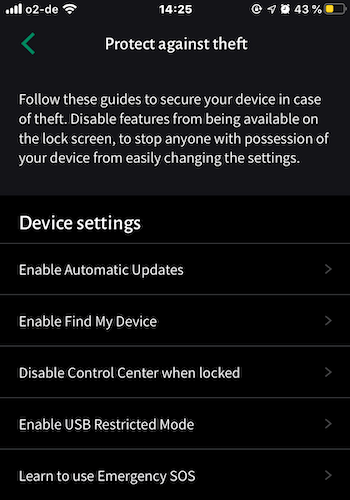
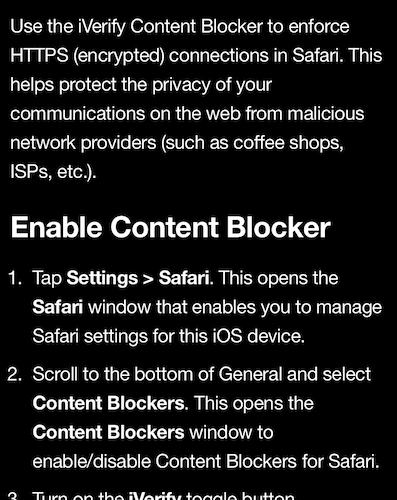
- For a task you haven’t completed, tap on it and the next page will give you complete instructions on how to achieve it, including a button to take you to the device settings.
- Once you’ve done it, come back to iVerify, tap I’ve Reviewed This, and it will be marked as complete. Move on to the next one and repeat.
iVerify Detects Threats to Your iOS Device
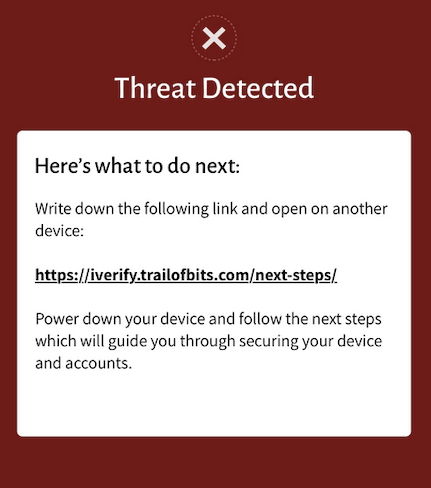
When iVerify detects a threat, it generates a unique link back to Trail of Bits, the developer which made iVerify. This link gives you information on what to do to eliminate the threat, as well as report the threat to Trail of Bits, to improve its threats database.
As the screen says, open the link on another non-infected device, close down the infected device and follow the instructions in the link given.
Not 100% Perfect – But Better Than Nothing
This should not be seen as a perfect solution to fighting spyware, malware, and hackers. Nothing is perfect. Threats evolve all the time, and obviously, if a government or state-backed bad guy gets involved, well then something like iVerify is going to be useless.
But 99% of us are not going to be targeted by totalitarian governments or someone using a voice scrambling device demanding they be paid a billion dollars in exchange for not messing up the power grid. For us ordinary folks, iVerify could prove to be a very valuable resource.




